Need Reliable Computer Services: Call (352) 224-3866
How Secure Is Your Key Management?
Written by Benjamin Syn on September 10, 2021 Under security
When it comes to keeping our data and communications secure, we often think in general terms like encryption. However, the lynchpin that makes any encryption work is the key. Whether it's the single symmetrical key or the pair of asymmetric public and private keys. These keys are what transform our message into meaningless cyphertext and back. Without the right key, this information is forever trapped as gibberish.
Yet, despite how centrally crucial our keys are, we never think about them. And with Key Management as a Service (KMaaS), we don't have to think about them. Instead, we can offload managing our keys to a professional.
What's a Key?
We talked a lot about symmetric and asymmetric keys in "What is Encryption, Types of Encryption, and Why You Need It." But I realized I never showed what a key actually looks like. So, let's look at a key.
If you look at the address bar, right in front of https://blog.nexgentec.com/ there should be a lock. If you click on that lock, you will see this webpage's certificate:
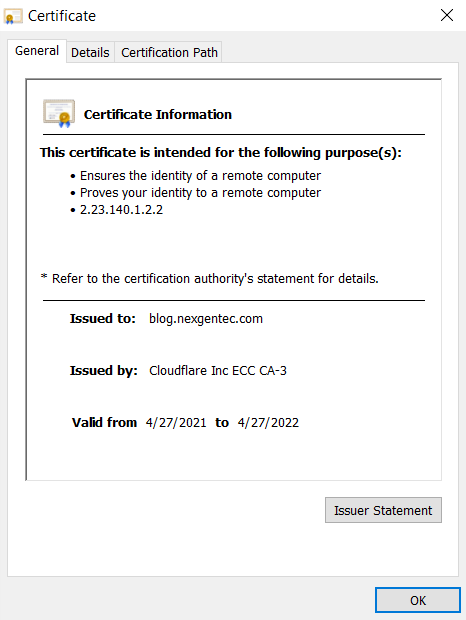
And if we click on "Details" and "Public Key," we can see our key for this very website:
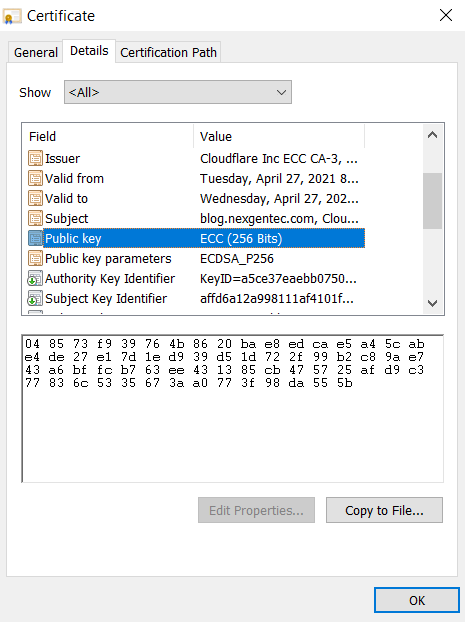
According to this certificate, this key is 256 bits in length and was generated with elliptic curve cryptography (ECC).[1]
Manage Them Keys … as a Service
This key is one of those public ones, which we give out to anyone. But what do we do with the corresponding private key? Exactly as opposite with how liberal we are giving out our public keys, we need to be militantly conservative with guarding our private keys. So what do we do with these to keep them from prying eyes?
Paradoxically, we give them to someone else. Specifically, a KMaaS provider.
There are many KMaaS providers to choose from. Companies like the Cogito Group and Sepior specialize in technologies like KMaaS. However, big names like Google Cloud Key Management and Microsoft's Azure Key Vault also offer key management services.
One of the wonderful features of a KMaaS provider is that they can divvy up our keys across multiple servers. In this way, if anyone server is compromised the hacker would only have a fraction of the keys needed to decrypt our data. But this is just one of the many features of a KMaaS provider.
You Gotta Keep 'em Separated
One of the biggest advantages of KMaaS is its separation of keys from data. When we place our encryption keys on the same server as the data these encrypt, hackers need nothing else. Once they compromise the server, our precious data is easily unencrypted and spirited away. It is like we are metaphorically locking the door but then leaving the key in the lock! Whether it’s encryption or locks, the keys have to be kept elsewhere for the security to hold.
In a microcosm of our network, this can be difficult to do. Saying we have multiple servers, we could keep all our data on one and all our keys on another. Or perhaps we could keep our keys on our computer. However, most networks defend themselves furiously from outsiders while allowing nearly unlimited access to devices on the same network.[2] If a hacker gets on to any device in the network, they can easily grab the keys over here and encrypted data over there and off they go.
All KMaaS providers do is manage keys. That's it. We assign the keys to them and then keep the encrypted data wherever. With the keys secure, and depending upon the encryption (of course), we could potentially leave the data out in the open. Without the right keys, this data is meaningless.
Keep Your Friends Close but Your Keys Even Closer
In addition to providing a place to distance our keys from our data, KMaaS providers can put some distance between our keys here in this nation and our data housed in another. Our data is subject to local law. And these local laws vary from country to country. The problem comes from that most major cloud providers are international corporations with servers all over the globe. They fling our data willy-nilly across this globe. This means that our data can end up nearly anywhere—and be subjected to those local laws.
Regardless though, a nation cannot access our data if they can't access the keys, so long as the encryption is powerful enough. It is one thing for a country to seize encrypted data and keys housed on servers in their jurisdiction. These countries can then do whatever they want with this data. And they can do this entirely without our consent or even our knowledge.
It is, however, an entirely different issue for a country to try to extradite our keys from us to access our data on servers within their border. First, there is no way for a country to do this—short of hacking us or our KMaaS—without our knowledge. Second, it can be very difficult for this country to establish a legal justification to compel us to hand over our keys.
Of course, we have to make sure that our keys don't slip out of the country or fall into the wrong hands.
Another Way
There is an alternative to KMaaS, of course. Just like an alternative to storing our data in the cloud is storing our data on a local server, and just like instead of opting for a subscription to some software as a service (such as Microsoft 365) we can purchase a license for the software (like Office Home & Business 2019), we don't have to use a KMaaS. We can purchase similar security with either a hardware security module (HSM) or a tamper-resistant security module (TRSM).
HSMs are costly. These specialized machines can generate these keys. As you may recall, creating a symmetric key is pretty straightforward and requires minimal computational overhead. However, asymmetric keys are something else. These complex mathematical keypairs can require multiplying vast prime numbers into truly enormous figures or calculating values from algebraic curves. As such, HSMs are primarily used by enterprise-level organizations to generate and store high-value keys. These keys are protected because their compromise could cause substantive damage to the organization.
TRSMs, on the other hand, are primarily used in financial devices such as payment terminals. Much like the message in Mission Impossible, the purpose of TRSM is to self-destruct if anyone tries to compromise the data that they hold. This way, if someone tries to brute force them, TRSMs are designed to destroy their data and keys rather than let this precious information fall into the wrong hands.
Speaking of which, just because an organization has an HSM, it does not mean that they always house these keys on this HSM. Many organizations opted to generate their keys with their HSM and then store these securely in the cloud with a KMaaS provider. This is known as bring your own key (BYOK).
But for those of us who cannot afford to spend the money for an HSM, many KMaaS providers offer the use of their HSMs. Here they spin up the key and then host it across their servers in an option known as hold your own key (HYOK).
Conclusion
There is a whole world out there when it comes to the keys that we need for encryption. Just when I thought I understood symmetric and asymmetric encryption, here comes KMaaS and HSM and TRSM—oh my! For those of us who would rather focus on our jobs than our keys, it’s nice to remember that there are professionals like NexgenTec who can help. We're here for you.
[1] Instead of multiplying enormous prime numbers.
[2] This issue is changing now that network professionals are moving more toward the zero-trust model.
Call Us: (352) 224-3866
