Need Reliable Computer Services: Call (352) 224-3866
(Pass)words to Live By
Written by Benjamin Syn on June 01, 2021 Under security
We want simple passwords. They are easy to remember. We want to use something like "password." Or an easy sequence like "123456" or "qwerty." Perhaps we offer a common interest like "football" or "ninja." While these passwords are easy to recall, they are also easy to crack. So, we take these simple passwords and trick them out. We replace letters with numbers to get "f00tball" with zeros. Or we replace letters with symbols to get "pa$$word" with dollar signs.
Try as we might, hackers can use brute force, dictionary attacks, and rainbow tables to figure out our best passwords. But we can fight back! Let's talk about some of the tools we can use to encourage bad actors to go after easier prey.
Break Your (Pass)word: Brute Force
Ignoring dictionary attacks and rainbow tables, how long would it take to brute force one of these passwords? Here's what Hive Systems and Secutiry.org have come up with: No matter what you do to a five-word password, hackers will crack it instantly, whether it's "ninja" or "n1nJ@." And modifying "qwerty" to "Q~3Ⓡty" will buy you five seconds.
In a vacuum, it would take a brute force attack the same five seconds to crack "password." And that's the key! Longer passwords are harder to crack. Period. A change as small as adding an s, "passwords," increases the time to brute force to two minutes. Making it ten letters, "mypassword," gets you nearly an hour. And an eleven-character password, like "mypasswords," would take a day.[1]
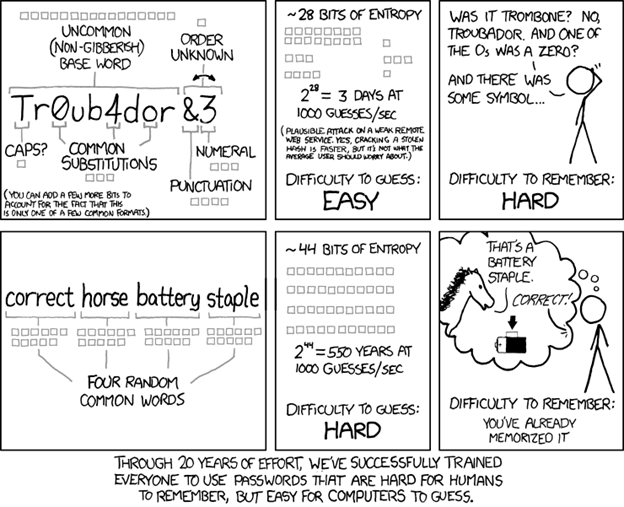
Figure 1. Randall Munroe succinctly offers the length is strength passwords in this classic XKCD comic.
Mum's the (Pass)word: Dictionary Attacks & Rainbow Tables
Everything I just said is true if the hacker is only trying to brute force your password. While a brute force attack is trying to guess each character, a dictionary attack is guessing entire words at a time. If the word is in the dictionary, then a dictionary attack will try it—and all the clever ways we might trick it out. As such, the five seconds that you thought you had from "password" is gone, as is the eight hours from "P@$$W0rd." A dictionary attack would crack these instantly.
Making this process even simpler, hackers have rainbow tables. These are the computed hashes for nearly every iteration of every common password. Having already calculated millions of passwords into hashes, this hacker needs to search for our hash. Once they find the same hash result, the hacker knows the password. As such, no matter how we modify "princess," "sunshine," or "dragon," a rainbow table will crack these passwords instantly.
What's the Good (Pass)word?: Making Users
With frequent data breaches of large companies, it has become a fact of life that our precious passwords are available online. To mitigate this, companies create policies that force their users to change passwords frequently, every quarter or even every month. System administrators likely believe that the more they make users change passwords, the more secure the network.
The problem is that these administrators that enforce this policy are discounting human behavior. The more they ask us to change our passwords, the more we are compelled to find ways to remember these. This policy creates new security vulnerabilities. Many of us now need to write these passwords on notepads at our desks to recall them. This issue is especially true when we enforce password changes every 30 days. Ninety days seems the happy medium. Even here though many add an increasing number to the password, going from "Password1" to "Password2" to "Password3."
Faced with this situation at my last job, this is what I did. I took a password, replaced some letters with numbers, and used these as a counter. Let's say my initial password was "Sch00ls!" After 90 days, I would add one to this making it "Sch01ls!" Ninety days later, I would change this to "Sch02ls!" As such, after my six years at this job, my last password was "Sch23ls!"[2]
Keep One's (Pass)word: The Password Manager
… or this would have been true has the IT department not introduced me to the password manager LastPass.[3]Password managers are incredible! These computer programs store, enter and even generate all the passwords that we use everywhere.
Between needing to have complex passwords that change all the time and needing a different password for each and everything, it has become impossible to keep all these passwords in our heads. The great news is that nowadays, we don't have to! Instead, we have password managers. These allow us to have incredibly lengthy and complex passwords unique to each website. And we don't have to remember any of them.
Well, alright, we have to remember the master password to our password manager. And this creates a problem all its own. If we use an online password manager, then all a hacker has to do is crack our master password, and they have all our passwords neatly organized in one place. This concern is legitimate. But this cost is more than worth the risk. Furthermore, we have a few ways to mitigate this issue.
First, your master password for these password managers should be epic. Since, in many ways, this is the last password[4] you are going to need this password needs to be lengthy and complex. Use every trick in the book. I recommend phrases or entire sentences complete with punctuation. And don't forget uppercase, numbers, and symbols.
Second, instead of a cloud-based password manager, there are offline options. Password managers like MYKI keep the password database solely on local devices and then sync these together. As such, instead of hacking our online passwords, with offline options, a hacker would need to get one of our devices. And then crack the passcode to get into the device. And then need to crack the passcode to MYKI …
At a Loss for (Pass)words: A Different Password Everywhere
We want a skeleton key that can open all our doors. One key that opens the house, starts the car, gets us into work, etc. Unfortunately, we have all these different keys for all these different locks.
Passwords are the same. We want one password to open all our accounts. One to rule them all. But different websites have different requirements, much like how my house key has teeth only on one side, but my car has teeth on both.
And this is a good thing. Having one password that we use for all of our accounts means that it takes only one password for a hacker to gain access to our entire life.
To address this concern, we often make a formula for each website that takes something unique about the website plus something specific about us to create an algorithm that is particular for each website. Perhaps my formula is the website + "Pa5$" (automatically giving us an upper, lower, number, and symbol). Gmail is "gmailPa5$." Outlook is "outlookPa5$." The concern here is that once someone figures out the formula (something that gets easier to do with each cracked password), it becomes simple to guess the rest of the passwords out there.
Once again, the best solution is a password manager. It doesn’t matter to me that my password to Gmail is "9Hzm42MmV63tY8Bf;M|b" and my password to Outlook is " JW7oyB57<G4eg6bC7u.O." I don't have to remember any of it. However, since many of us insist on actually knowing our password,[5] companies have come up with another way to authenticate users.

Figure 1. Here are the two most common passwords: "123456" and "qwerty"!
This too Shall Pass(word): Multifactor (or Two-Factor) Authentication
Having to remember myriad different passwords for seemingly every website and application has become untenable. And while password managers are an answer, they aren't the only ones. Rather than relying solely on passwords, more companies are turning to multifactor authentication.
In multifactor authentication, a website or application asks a few different ways for a user to prove who they are. The first is usually a username and password, which is something only you should know. Then it asks for some other form of identity verification. For example, it might text you a code to your cellphone, which is something only you have. Or it might scan your fingerprint or face, something only you are. Most of the time, this is a two-step process, so it is often called Two-Factor Authentication or 2FA.
Just for my Gmail account, I have five ways to offer this secondary authentication. First, Google very much would like me to use their Google app to authenticate. Second, I can use an actual authenticator app like Duo Mobile or Twilio Authy to get a one-time passcode. Third, I could authenticate with a physical security key over Bluetooth or USB. Fourth, I can use one of the backup codes that I have downloaded and saved somewhere. And fifth and most popular, Google can text or call me with the one-time passcode.
As we have gotten smarter in keeping hackers out, they have gotten smarter in getting in. To counter calling or texting our cellphones, hackers now port our cellphone number to their device. To port our number, all a person has to do is call the provider and pretend to be us. This ruse is easier than we want to believe, especially with some sob story about how important their lost phone is. To avoid this situation, we have to be proactive. We have to tell our provider that we do NOT want your number ported without our explicit permission.
Take My (Pass)word for It
There is nothing that can completely prevent a determined hacker from getting into our accounts. But there are several simple things we can do to make our accounts more work than their worth. We start with using as complex and unique passwords everywhere we possibly can. To help with this, take advantage of password managers like LastPass or MYKI. These allow us to have incredibly lengthy and complex passwords particular to each website and application.
Furthermore, utilize 2FA and multifactor authentication whenever possible. This second layer of authentication means that even if our passwords are compromised, our accounts remain secured. (So long as we tell our phone companies not to let our phone numbers be ported away to hackers …)
[1] As we're about to see, these times only work if hackers don't have access to a dictionary (attack). For these brute force numbers to be accurate, the passwords would have to be random. It would take five seconds to crack eight random characters like "irdbqbud." Two minutes for nine characters such as "rypaytpvs." Fifty-eight minutes for "clhtatjcyp." And a day for "myurhcztxuw."
[2] It sucks when employers don't have single sign-on. With different passwords for different applications, my sequence got out of order. For example, I was "Sch09lS!" for my email but "Sch02ls!" for the databases.
[3] Although, I think I had gotten up to "Sch12ls!" by that point.
[4] Hence the name LastPass.
[5] Not knowing a password amuses me greatly because, in cybersecurity, passwords are referred to as something you know.
Call Us: (352) 224-3866