Need Reliable Computer Services: Call (352) 224-3866
What is Encryption, Types of Encryption, and Why You Need It
Written by Benjamin Syn on August 31, 2021 Under encryption
Ransomware and cryptography? What does all this mean? And what does it matter? Today, we are going to get to the heart of it all and explore encryption. We'll look at the internet before encryption and after and examine what we encrypt and why. We'll talk about the two major types of encryptions: symmetrical and asymmetrical, and the various keys that these two systems use.
In "What Cryptography Is and What Are Cryptography Techniques," we introduced Alice, Bob, and Eve. We are going again to use these iconic cryptographic characters, and add to them, Charlie and Diane. Let's do it!
At the Beginning, an Open Internet
Despite our militaries using technology to encrypt communication decades before the advent of the internet, nothing was encrypted when the internet was pioneered. As we discussed in "When Good Encryption Goes Bad," usernames, passwords, and everything else was just sent in the clear. Anyone listening in on these early communications could read it all. Artifacts of this bygone era are the unencrypted ports that we once used.
- Port 20 to request files with the File Transfer Protocol (FTP) and port 21 to transfer these.
- Port 23 to remotely control computers via the command line with Telnet.
- Port 25 to send emails via the Simple Mail Transfer Protocol (SMTP).
- Port 80 to visit websites via Hypertext Transfer Protocol (HTTP).
- Port 110 to check our email either via the Post Office Protocol (POP) on 110 or port 143 for the Internet Message Access Protocol (IMAP).
And all of this communication was wholly in the clear, visible to anyone who knew how to look at it.
A Scared New World
Realizing what a terrible idea it was to openly communicate all of our private information with one another, we began encrypting our internet activity. However, since all the aforementioned ports were wholly in the clear, we needed entirely new ones.
- Port 22 to both remotely control computers via the command line with Secure Shell (SSH) and to transfer files with the Secure File Transfer Protocol (SFTP).
- Port 443 to visit websites via the Hypertext Transfer Protocol Secure (HTTPS)
- Port 465 to send emails via the Simple Mail Transfer Protocol over Secure Sockets Layer (SMTPS)
- Port 993 to check our email either via the Internet Message Access Protocol over Secure Sockets Layer (IMAPS) or port 995 for the Post Office Protocol version 3 over Secure Sockets Layer (POP3S).
By the way, while an email sent or downloaded over ports 465, 993, or 995 (or even 443 for webmail) is encrypted in transit, these are not encrypted emails. Read all about this in "You've Got Mail! But Is It HIPAA Compliant? Email and Encryption."
That said, let's look at one specific protocol to see why encryption is a good thing. Do you know how people joke about clearing their browser history? Well, until 2016, every website we ever typed into a browser was sent in the clear on port 53.
Yes, to get you to whatever site you desired, the computer had to query a Domain Name System (DNS) resolver. Computers don't know what "google.com" is. So, they need to look this website up in a DNS to get https://142.250.177.46 This DNS converted the words of a website into an IP address. And no, an incognito or private window doesn't hide this. (To learn more about this—and how there is a record of your entire internet history—go read "The Domain Name System (DNS) and Why Your ISP Records Every Website You've Ever Visited.") Every website that you have ever visited, up until a few years ago, was sent in the open for anyone to see!
Nowadays, we have DNS over Transport Layer Security (DoT) protocol on port 853. The first public resolver to switch to DoT was Quad9, but both Google and Cloudflare followed suit. Now, we can look up any website we want and keep it on the down-low (so long as we set up our DNS settings correctly).[1]
What We Encrypt
While our browser history can be embarrassing, there is a lot of private, personal information that we need to transmit over the internet, which we really don't want to fall into the wrong hands. Thankfully, one of the first things that we figured out to encrypt was passwords. This way, we were able to secure our online websites and applications.
This can be as innocuous as a credit card number we send to purchase something off of Amazon or eBay. Or something as confidential as our bank account information when we set up online bill pay. Imagine what an identity thief could do with our name, address, and social security numbers if they were to just intercept us e-filing our taxes. We're not even talking about Protected Health Information (PHI) covered by the Health Insurance Portability and Accountability Act (HIPAA).[2]Not only are all of these supposed to be encrypted, but so are all the aforementioned technologies, such as internet browsing and email.
And we need our communications encrypted so that our usernames and passwords don't fall into the wrong hands. If a hacker gets our credentials, they could perform malicious or fraudulent acts posing as us. Furthermore, these hackers could use our information to get between us and our work, email, or websites. Once they are the proverbial man-in-the-middle, these hackers can at best snoop on our data exchange and at worst change this information for malicious results, as we discussed in "Let's Get Physical … with Our Security."
These are just some examples of data that we want to keep safe with encryption. Other items that we want to keep secure include:
- Names
- Social security numbers
- Contact information
- Credit card information
- Financial account information
- Credentials
- Technical specs, research, and other sensitive data

Types of Encryptions - What’s the Difference?
To keep all of this valuable data safe, we need to change it into a meaningless form. To do this transformation, we need to take its plaintext form and encrypt it into cyphertext. We do this by using what is known as a key. When we want to reverse the process, we use a key to then decrypt this cyphertext back into meaningful plaintext.
The key(s) involved determining whether the encryption is symmetric or asymmetric. If one key is used for both encryption and decryption, then it is symmetric encryption. However, if one key is used for encryption and another key is used for decryption, then it is asymmetric encryption. Each of these has advantages and disadvantages compared to the other.
Symmetric Encryption
Let's say we are trying to share data, but we want to keep this data secret. In symmetric encryption, we share the same key. You use this to encrypt the data, and I will use this same key to decrypt it. Because we are using the same key for both tasks, the whole exchange requires relatively little hardware overhead. A symmetric key is usually no more than 256 bits. This means that almost any contemporary hardware can process symmetric encryption.
The issue with symmetric encryption comes when you or I want to share data with someone else. We would either have to share our key with a third party or they need to have another key that they share with you and a third key that they share with me.
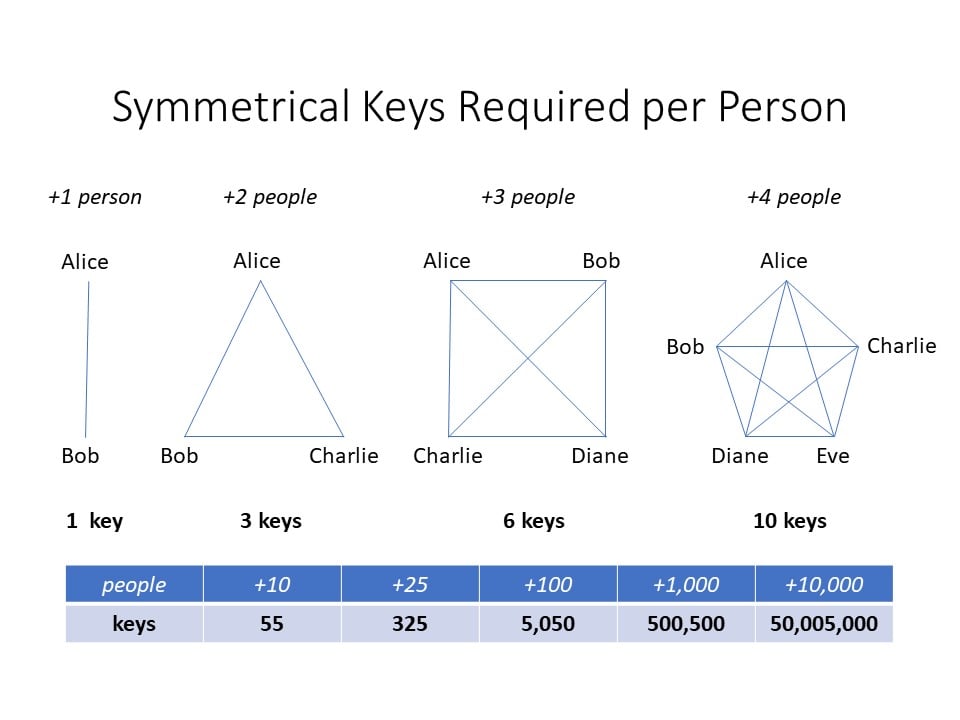
Here, Alice needs only one key for her and Bob to communicate confidentially. But if she and Bob want to communicate with Charlie, they need two additional keys: one for Alice and Charlie, another for Bob and Charlie (in addition to the first for Alice and Bob). This pattern is known as the triangular number sequence. In this pattern, the amount of keys needed is determined by adding sequential numbers. We start with 1 = 1, next 1+2 = 3, then 1+2+3 = 6, and 1+2+3+4 = 10. While this is fine at low numbers, would we want to do this for ten or a hundred or thousand people? Instead, let's simplify things. The equation for the triangular number sequence is:
xn = n(n+1)/2
One note: In our situation, we are talking about things from Alice's perspective. As such, it's Alice plus Bob equals one. Alice plus Bob and Charlie equal two. Alice plus Bob, Charlie, and Diane equal three.
Now we can figure this out easily. If our company has Alice plus five others, instead of adding 1+2+3+4+5, we could just do x5 = 5(5+1)/2 = 15. Perhaps symmetric keys would work if our company had only three employees, but imagine if we worked at Microsoft. As of 2021, Microsoft has 181,000 full-time employees. If any of these employee's keys get compromised, Microsoft would have to generate 181,000 new keys! And if Microsoft hired just one more person, they would have to generate 181,000 and one new key. So if they hired Alice, Microsoft would need x181,000 = 181,000(181,000+1)/2 = 16,380,590,500 symmetric keys.
There has to be a better option.
Asymmetric Encryption
Let's try this again with asymmetric encryption. Instead of our one shared key, we have two mathematically related keys. These keys are really neat because we can encrypt data with either one and then only decrypt it with the other. This one-way process is central to asymmetric encryption. While I could have one key and you could have the other, if each of us had our own key for everyone we want to communicate with, we would have the same issue as symmetric keys. (Recall the sixteen billion symmetric keys that Microsoft would require.) Instead of this, asymmetric encryption allows us to do something really cool.
Each of us has a pair of keys. That's it. Two asymmetric keys for each person. Period.
One of these keys is your private key. Only you have access to this double-secret key. And the other key we just put out to the public. We put it out there and freely give our public key to absolutely anyone. I know that seems counterintuitive, but it works.
Alice wants to communicate with Bob, so she encrypts the message using Bob's public key. She sends then sends this encrypted communication to Bob—and he is the only one at all who can decrypt it. Recall that asymmetric encryption is a one-way process. Once something is encrypted with a public key, the only thing that can decrypt it is the matching private key. When Bob wants to reply to Alice, he will get her public key and encrypt the communication. She will then use her private key to decrypt the message.
Therefore, a company with a hundred employees just needs 200 asymmetric keys instead of over 5,000 symmetric keys. And Microsoft only needs 362,000 keys instead of sixteen billion!
By the way, this process works in reverse too. That sounds strange, right? Why would I want to encrypt a message that anyone can decrypt? Because when I encrypt something with my private key, it proves to everyone that this communication had to specifically come from me. It's a digital signature. And, in fact, this process is what we are doing when we digitally sign something.
What Does "Mathematically-Related Keys" Mean?
Symmetric was so nice because we had just one key for everything. And it had a cute, little 256-bit key. Asymmetric, on the other hand, gets enormous quickly. An asymmetric key is often 2,048 bits or more. So, let's get into what makes this so complicated.
Asymmetric encryption relies on the fact that it is easy to multiply two prime numbers together but it is very difficult to get back to these original primes. While it's easy to take a result like 35 and pull out the primes five and seven, it gets harder to figure out the primes for a number like 321 (was it 17 x 19 or was it 11 x 31?). Now imagine that the primes aren't double digits like 11 or 31 or even 97, but primes that are a hundred digits like
- 1,814,159,566,819,970,307,982,681,716,822,107,016,038,920,170,504,
391,457,462,563,485,198,126,916,735,167,260,215,619,523,429,714,031 - And 5,202,642,720,986,189,087,034,837,832,337,828,472,969,800,910,
926,501,361,967,872,059,486,045,713,145,450,116,712,488,685,004,691,423.
Also, remember that these primes are the factors being multiplied. As such, the actual number that the computer is trying to break down is 10,000 digits long! Needless to say, factoring these enormous prime numbers requires vast computing power.
Unfortunately, our smartphones and tablets don't have that level of computational power (yet). Of course, these mobile devices get better all the time. As such, eventually, our pocket computers should have the power. The problem is that as the computational resources grow to generate these asymmetric keys, so do the resources to factor these large prime numbers. As Cloudflare's[3] Nick Sullivan explains, "As the resources available to decrypt numbers increase, the size of the keys needs to grow even faster." This race is untenable.
Elliptic Curve Cryptography
Thankfully, there is an alternate means to generate asymmetrical keys: elliptic curve cryptography (ECC). While I can follow something as straightforward as multiplying two large prime numbers, the math involved for ECC is well beyond my paygrade. According to Cloudflare's Nick Sullivan, "an elliptic curve is the set points satisfying an equation in two variables with degree two in one of the variables and three in the other" such as "y2 = x3 + ax + b." Let's just leave it at that for now, and I'll refer you to Sullivan's "A (Relatively Easy To Understand) Primer on Elliptic Curve Cryptography" if you would like to know more.
ECC, in addition to addressing the issue of key length needing to grow faster than computer processing, uses fewer resources. As James "Professor" Messer explains, "[ECC] uses smaller key sizes for the same amount of security, and it has a smaller storage and transmission requirement than traditional asymmetric encryption." This reduction of the encryption overhead means that even tablets and smartphones can participate in asymmetric encryption like this.
The Best of Both Worlds
Because of their use of computer resources, it is best to send larger files with symmetric encryption and reserve smaller files for asymmetric encryption. But what if Alice needs to encrypt a large file that she needs to send to Bob? Who can Alice trust with her symmetric keys? And how can she securely get my key to Bob?
Computer scientist and cryptographer Phil Zimmerman developed a fantastic compromise back in 1991. Here's how it works: Alice spins up a random symmetric key and uses it to encrypt her file for Bob. Alice then takes this symmetric key and, like a Russian Doll, encrypts it with Bob's public key! Alice then sends this larger symmetrically encrypted data and smaller asymmetrically encrypted key to Bob. While anyone who has the symmetric key could open the data, it would take Bob's private key to decrypt the key to decrypt this data. Zimmerman named this creation Pretty Good Privacy (PGP).
What Happens When We Combine Keys?
While not PGP, there's another neat trick we can do when we combine asymmetric keys: Alice takes her private key and combines it with Bob's public key. Bob then takes his private key and combines it with Alice's public key. Even though all these keys are different, due to their mathematical relationship to one another, they result in identical symmetrical keys. Now, Alice and Bob can communicate with each other symmetrically. And only the two of them have this symmetric key combination.
Beyond Encryption
While encryption is fantastic at securing our communications, it is only part of our security solution. For example, no amount of encryption will prevent someone from looking over our shoulder to see the data on our screens. For that, we need privacy screens. Furthermore, no matter which encryption we use, our physical computers are only secure if we lock the screen when we get up to use the bathroom. A seminal aspect is getting physical with our security.
We also can't simply trust using encrypted ports to encrypt our data. As we highlighted in "You've Got Mail! But Is It HIPAA Compliant? Email and Encryption," just because email may travel an encrypted route via the aforementioned ports 993 and 995 (or even port 443 for webmail) does not mean that this email is encrypted. For email to get where it needs to, the headers of emails often are sent in the clear. As such, although a snooper would have no clue what is in the body of an email, they would know that you sent an email to this specific person or organization—and could clearly read the subject line! This vulnerability is why the National Institute of Standards and Technology (NIST) advises sending email through a Virtual Private Network to encrypt everything.
However, sending an encrypted email does not mean that email remains encrypted. This exposure is one of the biggest issues. Email at rest on our computers or Google's servers are most often not encrypted. As such, our most personal correspondence is freely visible to anyone who can access these computers. Regarding email, this is why many people have turned to providers like Tutanota or ProtonMail, both of which provide encrypted email everywhere. Furthermore, ProtonMail uses PGP to ensure everything sent with this service is encrypted everywhere.
But what about the rest of our data. Microsoft explains, "When users travel, their organization’s confidential data goes with them. Wherever confidential data is stored, it must be protected against unauthorized access." As such, Microsoft encourages all users to utilize the BitLocker. This device encryption uses a wonderful little computer component—which is going to be a requirement for Windows 11—known as a Trusted Platform Module (TPM). Using the TPM, BitLocker encrypts all the volumes of a hard drive. As such, now if someone were to even steal our entire hard drive, it would be useless as it is wholly encrypted.
Encryption for Evil: Ransomware
Encryption is a tool. And like any tool, it can be used for good, like protecting our computers and our communication from eavesdroppers. Or evil, such as encrypting our computers against us with ransomware.
As we chatted about in "When Good Encryption Goes Bad: Ransomware," ransomware is essentially just encryption software. But this encryption is being used to keep us out. Computers and software don't know who's using them, they just follow their algorithms. And when it comes to encryption, they will decrypt their data for whoever holds the key. When you hold the keys, it's encryption. When a hacker holds the keys, it's ransomware.[4]
CLOSING
I know that all that is a lot to take in. And yet, we haven't even scratched the surface. For example, we missed how BitLocker relies on the Advanced Encryption Standard established by NIST. And we didn't even touch on how easy it is for quantum computers to factor impossibly large numbers and brute force traditional asymmetric encryption. If you want to know more about these or anything else, just let me know.
Otherwise, though, leave your encryption needs to your managed service provider (MSP). We are only too happy to help you encrypt your data, whether it's traveling in an email or at rest on your workstation or a server. And MSPs like us have incredibly powerful software to mitigate or even thwart most ransomware attacks. Just reach out to NexgenTec. And we'll do everything we can to keep your data safe.
[1] Contrariwise, you can prevent computers from accessing adult content (and block malware) by changing the settings to Cloudflare's 1.1.1.3 DNS resolver.
[2] For more on HIPAA and why no one should email PHI, check out "You've Got Mail!."
[3] If the name Cloudflare sounds familiar to you, it's because we talked about their DNS service, 1.1.1.1, in "The Domain Name System (DNS) and Why Your ISP Records Every Website You've Ever Visited" and we checked out their free VPN offering, also named 1.1.1.1, in "Work from Anywhere, Safely: Why You Need a VPN."
[4] Alright, technically, this is also just encryption, but the presumption is that this hacker has encrypted your data to extort a ransom from you for your data's return. Otherwise, why wouldn't the hacker just irrevocably destroy the data?
Call Us: (352) 224-3866